Microsoft AZ-104 Lab 02a: Manage Subscriptions and RBAC
Managing Subscriptions and Role Based Access Control in the Azure Portal
This lab is part of a series of labs I am using to study for the Microsoft Certified: Azure Adminstrator Associate (AZ-104) Certification. These labs are provided by Microsoft and can be found here.
In this lab, the focus will be on learning about Subscriptions and Role Based Access Control (RBAC), and how to properly manage these objects.
Lab Scenario
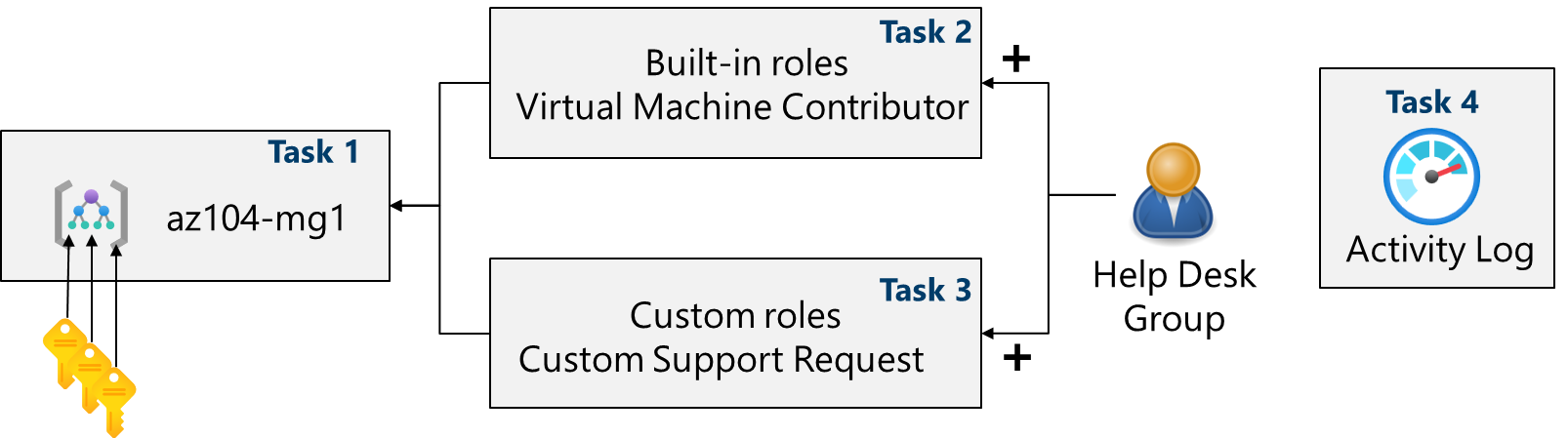
To simplify management of Azure resources in your organization, you have been tasked with implementing the following functionality:
Creating a management group that includes all your Azure subscriptions.
Granting permissions to submit support requests for all subscriptions in the management group. The permissions should be limited only to:
- Create and manage virtual machines
- Create support request tickets (do not include adding Azure providers)
Task 1: Implementing management groups
In this task, we will create and configure a management group. User accounts will store user data such as name, department, location, and contact information.
Go to Management Groups and select Create.
For our management group we will use the following configuration:
| Management Group ID | bigcyber-mg |
| Management Group Display Name | bigcyber-mg |
Once we have created the management group we can see it displayed on the Mangagement groups page:
Task 2: Review and assign a built-in Azure role
In this task, we will apply a built in Azure role to a member of a group using our new management group.
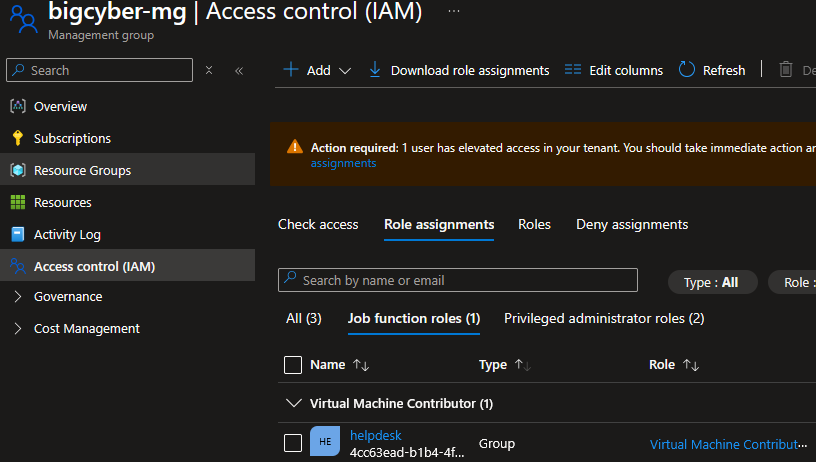
For our purposes we can add the “Virtual Machine Contributor” role assignment to the helpdesk group so that they can assist in managing VMs.
After hitting Review + create, we can see that our role assignment exists for the help desk group.
Task 3: Create a custom RBAC role
In this task, we will create a custom RBAC role that can be applied to groups in the future. Custom RBAC roles allow us to assign specific permissions and separate their distribution by role assignment.
From our bigcyber-mg management group menu we can create a custom role. For our purposes we will create a role for Custom Support Requests for the helpdesk group with these configuraitons:
| Custom Role Name | Custom Support Request |
| Description | A custom contributor for support requests |
In Azure, we can clone a Microsoft premade role and edit the specific permissions to better suit our role. For this custom RBAC role, we will clone the premade Support Request Contributor role.
From this role, we want to exclude the Microsoft.Support Other: Registers Support Resource Provider permission. This can be used to change the Support resource provider, which is beyond the scope of a helpdesk roles duties.
Excluding the unwanted permission, we can see in the roles JSON file that the specific permission was added to the notActions category:
Now that we have our custom role we can repeat the steps from Task 2 and assign the role to the helpdesk group.
Task 4: Monitor role assignments with the activity log
In this task, we will learn how to read the activity log and filter for specific events.
By navigating to our bigcyber management group and selecting the Activity Log blade, we can see all the logs generated by our actions in the group.
Here a log has been generated for our role assignment and custom role creation:
Key Takeaways
In this lab I demonstrated my ability to:
- Create Management Groups
- Assign Roles
- Create custom RBAC roles
- Monitory activity logs
Thank you @Microsoft for the great labs to prepare for the AZ-104 exam. Check out their series of AZ-104 labs here.